Secure DMs and groups might be how Nostr wins. Like Signal, but better: no phone number or centralized service provider needed. Actually there are no publicly visible user IDs involved, so in that regard it's similar to simplex.chat.
Unlike public messaging, DMs do not depend on the network effect. Great for onboarding people and keeping them returning with push notifications. They get a bitcoin wallet, zaps and all the other Nostr greatness on the side.
Many people don't want to let go of their existing follower base on X, but "Nostr DMs only" is easier to do. I could imagine that becoming a thing in the Bitcoin scene at first.
Thread
Login to reply
Replies (47)
Totally agree! Secure #DM and #Groups. This will bring more people in. And it will open up people to use better technology and better money. #Bitcoin
#nostronly
secure powerful community
our goal is to create a beloved community, and this will require a qualitative change in our souls as well as a quantitative change in our lives
- Martin Luther King Jr.
I would want DMs that disappear when the DM window closes.
If Nostr could implement Twitter Circles, which Elon killed, that would be amazing. It was nice being able to limit post visibility to certain followers.
Doesn’t NOSTR DMs have the issue that even if the contents of the message is encrypted, the relays are still broadcasting the message to a publicly known address? Like you can see who is messaging each other, even if you can’t see what they’re saying.
Or can nPUBs create subaddresses and obfuscate that away?
Yes!
Bitcoin and chill
My concern is that anyone can spin up a set of keys. Session had a massive DDoS attack on their open groups earlier in the year and that was because there was no limit to how many Session IDs can be spun up. We also saw Nostr get hit with the ReplyGuy spam recently as well, due to similar issues.
People love to criticize Signal for its phone number requirement but that requirement helps keep the spam and attacks on the network at a minimum. To me, the issue isn't the metadata, it's whether or not that metadata is properly encrypted and obfuscated. Signal does both thanks to features like sealed sender (which makes it virtually impossible to determine where a message came from, making it way harder to conduct any sort of MITM snooping).
I'm purple pilled but I think we have to recognize that Nostr isn't the solution to every problem, just as Bitcoin isn't the solution to every problem. Both are phenomenally powerful and important to our future, but they're not the only things we'll need to secure our digital freedom going forward, and there's no reason we need to stretch their capacity when other tech already offers the functionality we're looking for. I mean, Session itself offers all of the functionality we're talking about here, the only downside is the lack of zaps (but really, who needs zaps for private messaging?).
That being said, I DO agree that Signal having a centralized server infrastructure isn't ideal. It'd be cool if they'd open it up to volunteers hosting nodes similar to Session and SimpleX. Volunteers can already run Signal proxies so why not let them host nodes and gradually move things over to a decentralized framework? There's no reason Signal Foundation couldn't rent out cloud space during times that the network is overwhelmed, especially since being decentralized would cut down on a huge chunk of their operating costs.
Finally, I also do agree that it'd be nice if Nostr would at least set up E2EE for DMs, considering the fact that Nostr has a bit of a permanence effect on notes shared via the relays.
Signal uses the same mainstream encryption protol as Meta's whatsapp. No thank you.
Telegram, with its home brew mTproto encryption was heavily criticized by the mainstream geniuses. But the governments had no issue with signal? very strange....sounds like it wasnt a threat to them at all but telegram was! telegrams encryption was clearly superior hence why it pissed them off. Too bad it was centralised for the normal messages. The E2E secret chats are probably still reliable.
But i wont trust a centralized service ever again or something like Signal that uses phone numbers, leaks meta data and uses google and meta technology.
simplex or bust
More like WhatsApp used Signal's protocol. The Signal Protocol was in existence before WhatsApp started using it. It uses that protocol because of the fact that it's the gold standard of end-to-end encryption protocols.
Telegram's protocol was criticized because it was vulnerable in various ways that Signal's protocol was not. Encryption experts cross the world pretty much universally agreed on that. The reason why governments don't go after Signal, but they went after Telegram, is because Telegram didn't encrypt all that much. In fact, it only encrypted things if you specifically told it to. There'd be no reason for governments to even try to go after Signal if everything's encrypted and that nothing can actually be taken from it. In fact, governments have tried to get data from Signal, but were unable to take anything because of how everything is encrypted except for basic data like when a person first started using the platform.
It's ironic that you're talking about all of this while supporting SimpleX, which is backed by a for-profit corporation and is relatively new to the field, thus meaning that they have not been proven quite like Signal has been. By all means, SimpleX is a very neat tool that I am very much looking forward to seeing the future of, but if you want security, you really can't get better than Signal. This isn't just my opinion either. This is the opinion of virtually every security expert, cypherpunk, etc. Edward Snowden himself recommended it, and if someone with such a high threat model is confident in using it, then average Joe on Nostr can use it.
I see who is paying you. The globalist venture capitalists who want to prevent people from using tools that threaten them.
Good luck to you.
oh youre a shitcoiner.
now it all makes sense.
Also, as an addendum, Signal does not leak metadata, that is blatantly false. The only metadata that anybody can get is stuff like the frequency of a message being sent, and you really can't cut down on that kind of metadata, even with SimpleX.
In fact, Signal has a feature called Sealed Sender that makes it so that, when you receive a message, anybody spying on the network can't see who that message came from. If you and all your contacts are using Sealed Sender, then there's really no way for them to truly figure out who you or your contacts are unless you doxx your contacts through other means, such as using, well, Telegram.
Maybe you could ask them to get in contact so I can actually have some money in my life. Heh, that's a joke. But the truth is you can talk to anybody, especially people who actually are professionals in the sphere, and they'll tell you the exact same thing as what I'm saying. You're free to use whatever platform you want, but don't pretend to have superior security just because you don't trust the "mainstream" platform as if Signal is somehow mainstream.
Again, if somebody with the literal full force of the U.S. government against him is okay with using Signal, then I think you can use Signal.
If you think that promoting very practical options such as Monero alongside Bitcoin makes me that, then yeah, I guess so. People like yourself are exactly why outsiders view Bitcoiners as a cult.
if someone with the literal full force of the US government doesnt have a problem with Signal, then Im not convinced.
Why did they have a problem with telegram and not with signal? because they were worried about you becoming a victim of the mTpro encryption? lol
yeah this is a little beneath me, sorry.
Signal "leaks" metadata because everything goes through their servers.
They can't see the contents of messages, of course, but they can see everything else.
At least to the extent that they have information about users.
Simplex fixes this, that's what it was designed for.
You're misreading what I'm saying. Edward Snowden is one of the most hunted men by the US government, and yet he uses Signal, so that's all you really need to know about that part. If the government had access to Signal, they wouldn't need to hunt him so hard. They'd just get access to his information. It's not backdoored and that's proof.
And no, the reason why they went after Telegram was because there was information that they could easily get from Telegram. They can't do that from Signal. They've tried and they failed. Again, if the government thought that they could get anything out of Signal, they would be doing the exact same thing they're doing to Telegram right now, but they realize they can't, so they don't waste their time. Instead, they redirect their efforts to compromising individuals opsec. That's the real threat to Signal: poor opsec. Detractors commonly point to the Tucker Carlson "hack" but that wasn't a hack or a flaw of Signal, that was a flaw in his own personal opsec.
That's a bit of a stretch. The only metadata that it actually "leaks" is the frequency of your messages and your IP if you're not using a VPN. The thing is, a VPN can hide the IP easily, the frequency of messages issue is going to happen with any messenger. With Sealed Sender, metadata isn't a concern unless you dox yourself. And if you do that, then that's on you, not on Signal. And even if you do that, sealed sender still makes it impossible for any snoop to actually see where messages are coming from.
Thing is, even with other messengers like Session or SimpleX, if government authorities are paying attention to multiple contacts in the same circle, they're going to know who is actively sending messages, whether it's through Signal or one of those anonymous messengers.
The only advantage to using an anonymous messenger is to speak anonymously with people you don't know in person. If you're talking to people over the internet and you want to stay completely anonymous, then it has a purpose. It's for the same reason that people say you shouldn't sign into accounts on Tor because it immediately de-anonymizes you unless that account is exclusively used on the Tor network. At the end of the day, using an anonymous messenger to keep in contact with people you actually know in person is not any more secure than using Signal.
And that's without diving into the whole subject of SimpleX being run by a for-profit corporation instead of a non-profit organization, which is concerning in and of itself.
I understand that they're encrypting the sender information, but they can still do timing analysis on IP addresses and when messages were sent, because it's all flowing through a central server.
So, OK, it's an overstatement to say that they can see who's messaging who and when, my apologies.
also shitting on a company as being for profit ia dumb. it's a valid data point, but you can't say that therefore they're compromised and less trustworthy.
We could just as easy to criticize signal for having WEF members on their board.
What can they get from end to end encrypted secret chats in telegram?
nothing. not even with Durov in custody.
That doesnt make me a supporter of Durov or telegram, just stating the facts.
Since you insist on discrediting Simplex while glorifying Signal, here are some more facts for u...
1. User Identification
Signal: Uses phone numbers and usernames for identification.
SimpleX: Does not use phone numbers or usernames. Instead, it generates randomized user IDs for each conversation, which are sent via QR code or link.
2. Server Control
Signal: Has a centralized server structure, with a single entity controlling the infrastructure.
SimpleX: Offers decentralized servers, allowing users to self-host or participate in public servers. However, SimpleX still controls which servers are integrated into the network.
3. Metadata Protection
Signal: Has a strong reputation for protecting metadata, but some users may still be concerned about the centralized architecture.
SimpleX: Touted as having stronger metadata protection due to its decentralized design and use of one-way queues to mitigate communication correlation.
4. Disappearing Messages
Signal: Offers disappearing messages (ephemeral messaging).
SimpleX: Does not have this feature.
5. Self-Hosting
Signal: Not designed for self-hosting.
SimpleX: Allows users to self-host servers, providing greater control over data and infrastructure.
6. Popularity
Signal: More widely recognized and used, with a larger user base.
SimpleX: A newer, less well-known application, but gaining popularity among privacy-conscious users.
Conclusion
Signal and SimpleX cater to different user needs and priorities. Signal’s centralized architecture and familiar UX make it a good choice for those already invested in the ecosystem. SimpleX, with its decentralized design and focus on metadata protection, appeals to users seeking greater control and anonymity. Ultimately, the choice between Signal and SimpleX depends on individual requirements and preferences regarding privacy, security, and usability.
Sure, but that's a flaw with all messengers, even decentralized ones. The reason I see Session as more secure is because of the onion routing. Thrice encrypted and bounced across the world. SimpleX decentralization isn't conducted that way. It's better than nothing but most of the servers are hosted by the company and seizing those servers would get you a lot more metadata.
Also, yes, them being for-profit is completely relevant and concerning. A for-profit corporation has to maximize profits, meaning they aren't quite as trustworthy to host a privacy service. Meanwhile, a non-profit doesn't have to go wild to maximize profits. They actually directly have a necessary reason to do what they claim they're doing or donations will dry up.
I will be replying to this in-depth later.
Okay, first off, yes: they can get loads of metadata from secret chats on Telegram. As far as I'm aware, nothing but the messages themselves are encrypted on Telegram secret chats; this is a similar flaw to Matrix. Sure, keeping the messages encrypted is supremely important, and yes, I think both Telegram and Matrix have plenty of valid use cases. However, metadata is very important as well, and Telegram doesn't encrypt much of it (if any). Signal encrypts pretty much everything they can possibly encrypt. Moreover, Telegram's encryption standard is widely panned by cryptographers and security experts due to various flaws; there's literally zero reason for an app to not use the Signal protocol or a fork of it. Durov just wanted to be different, as his recent slander of Signal proves.
Regarding SimpleX, I'm not discrediting it. I'm simply expressing valid concerns over it. I'm not against it, I use it too (though not much, because it's slow and janky at this point). I'm just not sold on this idea that it's somehow the perfect, maximum privacy encrypted messenger. Signal is almost universally accepted by security pros and cryptographers as the best, or at least one of the best options for secure messaging. Again, if the most wanted man by the three-letter agencies of the United States (Edward Snowden) feels comfortable using Signal for his messaging, then random, average joes on Nostr have no excuse for hating on it because none of you are even remotely as important to intelligence agencies as whistleblowers like him. Preference is fine, don't get me wrong: you're 100% free to use what messenger you like best and I think that's great! However pretending like Signal is some honeypot or heavily flawed because you think you know better than the people who study these topics as a career it really does make y'all look like you're talking out of your backsides. Now, on to the individual points.
1) Signal verifies with a phone number, usernames make it so you never even have to reveal that number to anyone. This is the same as Telegram except, unlike Telegram, Signal actually keeps all of that metadata encrypted. SimpleX does have unique IDs for each conversation, which is nice for privacy, but it can also easily lead to abuse on the network. Session, which has cryptographic IDs, proves this is more than a possibility; earlier this year, Session's open groups were unusable and the entire network slowed to a crawl, all because some dork in his mommy's basement ran a massive DDoS attack mass-spamming ads for a group that he claimed was a CSAM group. Signal having phone number verification means that you don't see quite that level of abuse on the network or its bandwidth. Decentralization is great and all, but if you're combining decentralization with unlimited user IDs, that's a recipe for disaster, and a messenger that is incredibly slow and non-responsive is not useful in any way.
2) I'll give you this much: I do wish Signal was decentralized or, at the very least, offered a hybrid decentralization (basically, running off of volunteer nodes unless the network is overwhelmed, during which it'd hop to cloud providers). However, I also can't blame them for not doing that since it'd likely require a total rewrite of the code and really, all the decentralization gives to an encrypted messenger is that you have less likelihood of downtime.
SimpleX decentralization is a thing, but it's only "decentralized" in the sense that it has various nodes, a majority of which are run by -- you guessed it -- the corporation developing SimpleX.
3) The only metadata Signal "leaks" is the same kind that other messengers leak. If a hostile force obtained the servers that SimpleX is routing messages through, they can still get that metadata. You can't stop this, the only way to get around it is to use a VPN or Tor. In fact, if you're using an "anonymous" messaging app without a VPN or Tor (one or the other; don't mix for a single user ID), you're essentially putting all your eggs in one basket.
4) I mean, disappearing messages are pretty important. The fact that the "ultimate privacy messenger" doesn't have a very basic feature of private messaging is questionable at best. That said, can't individual groups set a timeout for messages on SimpleX?
5) Self-hosting is a great concept but in practicality, very few people can or even want to self-host. Moreover, the fact remains that the overwhelming majority of SimpleX nodes are hosted by the company, not volunteers.
6) Security by obscurity is important. If only a handful of people use SimpleX, then you're not as private or anonymous as you would believe, because as I said, metadata like your IP is still present. If you're not using a VPN/Tor, anyone watching the network can see you're using Signal... OR SimpleX. The difference is that Signal is massively popular, meaning you blend in with millions of other users around the world, whereas SimpleX is newer and less populated meaning you have risk of being singled out by ISPs or government snoops.
Not sure why you felt the need to go with an AI-generated reply but I figured I'd address the things you're trying to present as alleged issues with Signal, regardless of the AI reply.
i'm just gonna repeat myself endlessly about this until people fully grasp how simple it is
p2p messaging is only possible with inbound routing, and the establishment has dragged its feet about allowing this and deploying ipv6 that would enable people to run servers on their home computers easily
a workaround that is really simple is to use reverse proxies and have the protocol use http/s and people can run servers on VPS that connect to their relays via wireguard
nostr goes further with teh outbox model and already, clients that support outbox can directly connect to relays their friends set as their inboxes and drop their DMs straight in them
this can even be done on mobile devices
what it doesn't give you is asynchronous messaging but what it does give you is metadata privacy and full control of your own data
I like the idea, but there are serious problems with leaking metadata with #nostr DMs. Not sure people care, but having the ciphertext available to everyone is a risk.
It can be mitigated by having a unique relay for each group, but requiring people to do advanced relay management is not a recipe for success.
This could be fixed at the protocol level. E.g.
Client: give me the encrypted notes for key ID 0xabc123
Server: Sign this nonce with that key and they're yours
Client: here's the sig
Server: here's the encrypted DMs
It still lets the relay see who is messaging whom, when and how often, but that is very much like Signal. But unlike Signal, nostr could pick a different subset of relays for each message so no single relay has all the information. As long as everyone in the group is using the same set of relays, that should be reliable.
nip17 dms pretty similar to what youre saying. it works.. not all clients wanted to implement. those that did, a glimmer of hope was had 🙏
We have DMs with groups on Simplex. And hiding meta data is critical if you value security. Bill Binney, retired head of tech at the NSA, said meta data tells them almost all they need to know even if they can't read the actual messages. That's probably why most corporations will allow you to install Signal on your phone but will block Simplex installation. Signal is a meta data honeypot.
I am still pissed that nostr, that advertises itself as decentralised and censorship resistant, managed to slap a "sensitive" viewing ban on one of my posts, that not even I could read and then deleted my protestation !? FFS !! Highly suspect.
As it stands, Simplex may end up to be the solution
But how I use them? I'm on Amethyst
DM´s need to be deleteable - which is not possible at the moment.
And they shouldn´t create any metadata = the hardest part!
Messenger with a short ID and no metadata are available = it´s called Threema!
Check for yourself and visit:
Rate:
🟩=3
🟨=1
🟥=0
Results (and where the money comes from)
1. Threema = 83 = most secure Messenger (User pays one-time + BTC possible)
2. SimpleX Chat *= 79
3. Signal (OTF / Brian Acton / Ex-WhatsApp) = 77
4. Session (Loki Coin & suspicious Chinese) = 77
5. Wire (Janus Fries / Ex-Skype) = 68
6. Wickr (Amazon) = 61
7. Element / Matrix (Amdocs / Morris Kahn) = 56
8. Apple iMessage (Hardware sales) = 37
9. WhatsApp (Meta) = 32
10. Google Messages (Ads) = 28
11. Telegram (Putin) = 27
12. Facebook Messenger (Meta) = 26
13. Microsoft Skype =10
* SimpleX Chat got 380.000 $ from VillageGlobal.vc = Jez Bezos, Mark Zuckerberg, Bill Gates, ect. Plus Jack Dorsey and other Venture Capital Companys!
OFT = OpenTechnologyFund = US-Goverment
If you want to buy Threema, you can buy a license (Android only) from me and pay with Bitcoin Lightning! Ask for my Threema-ID or just contact me via nostr!
Secure Messaging Apps Comparison | Privacy Matters
This site compares secure messaging apps from a security & privacy point of view. These include Facebook Messenger, iMessage, Skype, Signal, Simple...
Just saw Threema's website again. Seems like they are open source now and tout Swiss data residency. Back in 2016 I was considering secure alternative to WhatsApp but then signal had just started to mature. Threema I believe was closed source, Germany based company, and required upfront payment limiting network adoption. Good to see them evolved, thanks for sharing!
How would you create a message without Metadata? That's pretty impossible
Also, working on deleting dms is a waste of resources, you can't unsend a letter, you can't unsay a sentence, you don't need to be able to delete dms as long as they are secret.
they are deleteable if the relays support delete, which is yet another reason why paying for relays is just going to become normal
in my relay implementation all event kinds can be deleted except delete events themselves, they are there as part of ensuring the event is not saved again (it also includes a special tombstone index field that refers to the event id and is searched for when performing a delete)
the other thing about it is that normally you can't delete events authored by other users
this is a good reason why it would be useful if the relay always checks your mute list and so if you have a scammer message you, once you mute them, the event stops being returned from the relay
it's not hard to see how all of these use cases make it abundantly clear that users should only need to keep a few relays, that the relays should have smart filtering features (i'm going to implement this mute-filter feature soon, making a mental note) and that the relays need to be paid relays, so that this kind of functionality, related to issues of confidentiality and privacy has incentives to be implemented
free relays are a slippery slide down back into the hell of feed manipulation and market data harvesting
I dont like how Threema purposely misleads and lies to users on their comparison chart. I barely looked at threema for 30 seconds and this is what i see on their webpage:
"Telegram is not encrypted messaging".
This is clearly a lie despite all the other shortcomings of telegram, could have just told the truth and make it easy.
For this lie, they cannot ever be trusted nor should they ever be trusted.
Simplex rules.
Telegram got ZERO dataprotection.
And NO encryption at all.
Telegram hardly qualifies as an encrypted messaging app since it doesn't have end-to-end encryption enabled by default, and there's not even an option for group chats.
If Simplex already does this (and arguably way better) then why would this bring people to Nostr?
There's nothing novel here. Not even for the supersecret activists. Also, why would they even want to tie their npub to any of it?
Ratchets are crappy UX on an open protocol rich in all these other content types.
All this quadruple ratcheting also ignores Relays as more efficient and interoperable solutions for 90% of what they're trying to do.
Chat relays, btw, are where an actual UVP can be found. They can be the Telegram 10x experience you encryption-schene-geeks keep hyping people into.
If we can do it all on Nostr, let's try. Built from the ground-up, the right way.
Simplex does secrecy better, just as many other things have done things better than Nostr, at one point or still do.
If I can use my npubs to log into everything, whilst preserving my privacy, degree of anonymity and security, I'd like that and I know many others will too.
It's all about giving options.
It might just get other services such as Simplex to somehow integrate Nostr in one way or another (perhaps not identities, but other things).
At this point in Nostr's development, shooting down possibilities is like suggesting why use Nostr instead of something else.
For the past decade we've had to install tons of apps for tons of social circles with no interoperability.
Let's give interoperability a proper go, perhaps without sacrificing the rest, and we'll see where we land.
What about this? Any cause for concern?
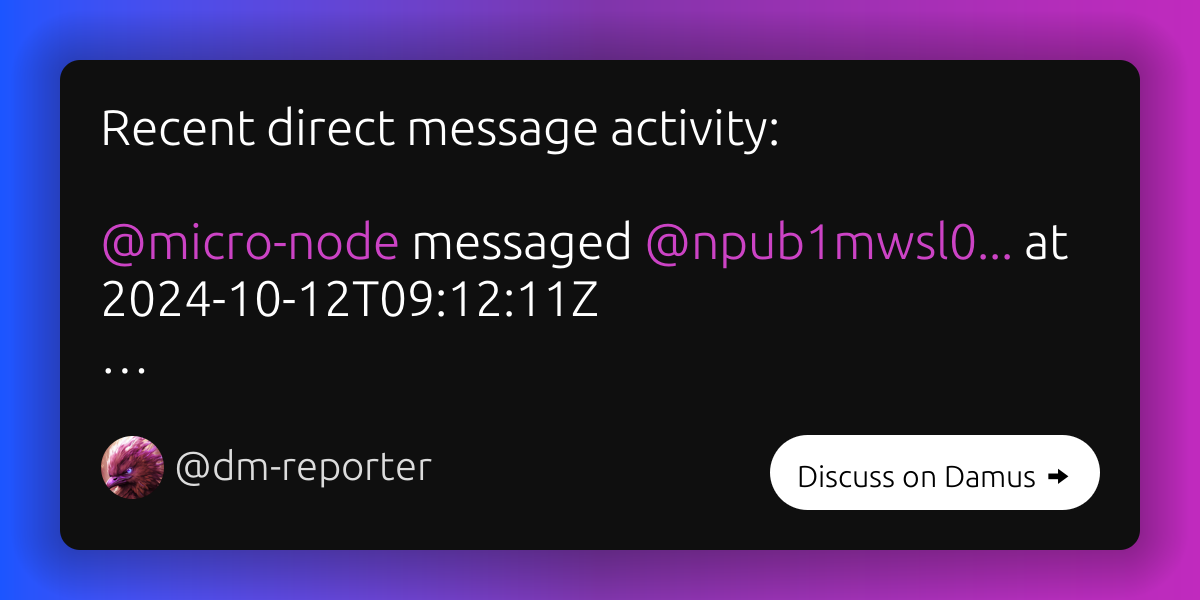

Damus
dm-reporter on nostr
Recent direct message activity: nostr:npub1me48869w43j30cfry9ay
Leaking metadata ? I am very disappointed with nostr. No effective DMs, no Groups, metadata leaks , not true decentralisation and centralised censoring. Simplex has all this fixed already. Nostr is reinventing the wheel with a worse wheel
The sketchiest part to me is that nobody is talking about this. Seems like a major risk to me.
I am all for innovation and progress, but mindless cheer leading and completely ignoring glaring problems is very odious. Lots of that here. I get very suspicious of another motive when I see that.
good thread! t-y
it might 🤷♂️