Me: Fine. I'll sign up to use a passkey to log in to this particular service. So many people tell me passkeys are the obvious thing to do now. Maybe the experience has gotten better in the last few years since I tried. [Signs up on desktop with 1password]
Service, a week later, on their mobile website: Please sign in with your passkey.
Me: [presses button]
Service: We couldn't find a passkey in your mobile web browser.
Me: Uhhh it's in my 1password app vault?
Service: lol what's that
Darius Kazemi
Darius Kazemi
npub1fd2l...f2f9
I'm the administrator of this server. https://tinysubversions.com is where most of my stuff lives. I make Hometown along with a bunch of other fediverse software (see pinned posts). I'm trying to fix the internet, and some people say I'm at least kind of succeeding. Based in Portland, Oregon, USA. he/him
Website: https://tinysubversions.com
Podcast 1: https://explainjojo.com
Podcast 2: https://toomuchnotenough.site
Working on the internet at: https://asml.cyber.harvard.edu
My favorite thing on Bluesky is a labeler made by the Social Technologies Lab at Cornell Tech.
It surfaces metadata on posts. Most useful to me is "This person posted more than 50 times yesterday."
It recasts a post like the one pictured. It reminds me to look at their profile and figure out if they are a real person, and are they terminally online, or engagement farming, or what. Then I might block/mute because I don't need people like that in my lifeworld.
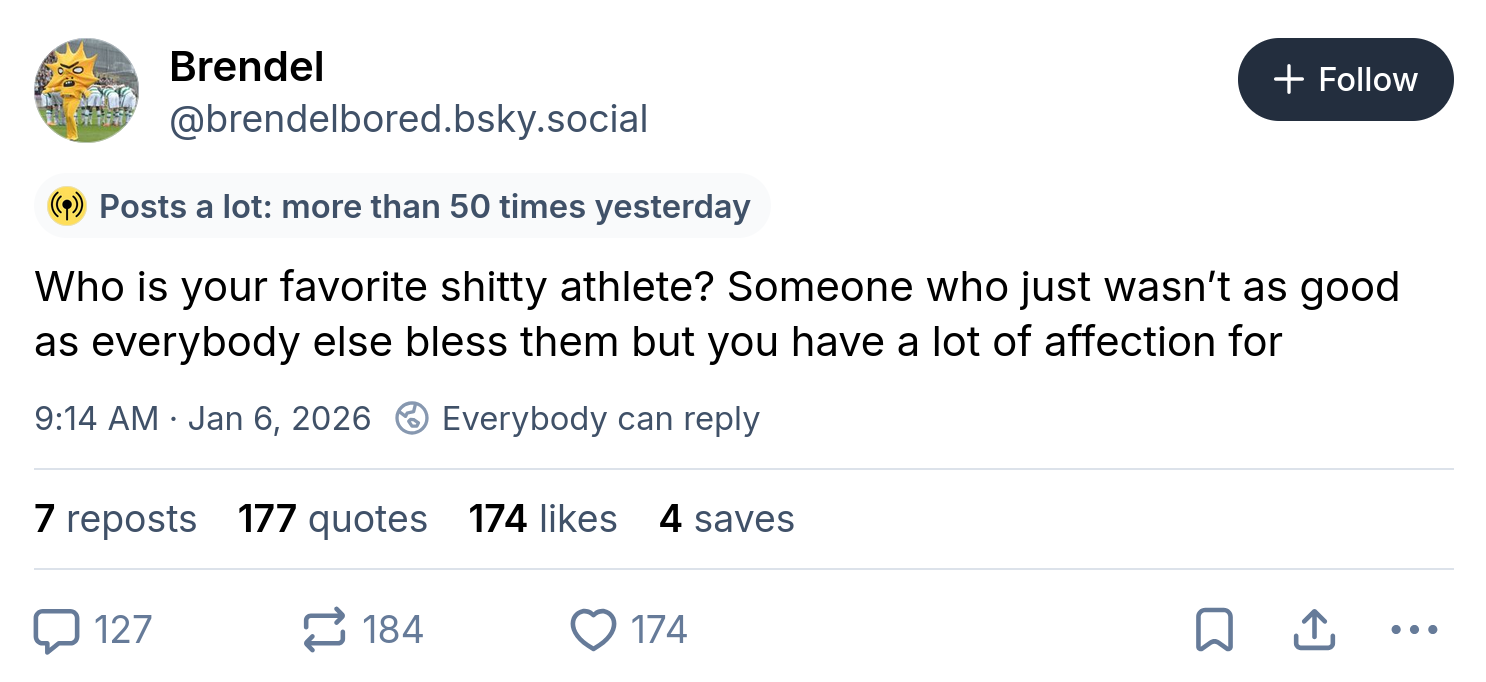
Bluesky Social
stechlab-labels.bsky.social
A research project from Cornell Tech, investigating using automated signals to help users have more context about the accounts they are interacting...

> delphitools is a collection of small, focused utilities that respect your privacy and work entirely in your browser. No data leaves your machine, no accounts required, no tracking. Just tools that do what they say.
delphitools
A collection of small, low stakes and low effort tools. No logins, no registration, no data collection.
Seeking advice. I have many services that require cert renewal for HTTPS. My usual workflow for nginx is:
1) set up a cron job to call certbot monthly (strictly more often than needed for a 90 day cert but I'm lazy)
2) 91 days later, re-cert fails, realize that there was a bug in my script, fix it
3) 91 days later, re-cert fails, realize there was a bug in my script, fix it
4) at this point it probably now works forever
Is there a good way to test things properly so I skip steps 2 and 3??
You discover a file on your hard drive called "eggn.ogg". You play it. What does it sound like?
I think I'm addicted to assembling uniforms for nuns... it's habit forming