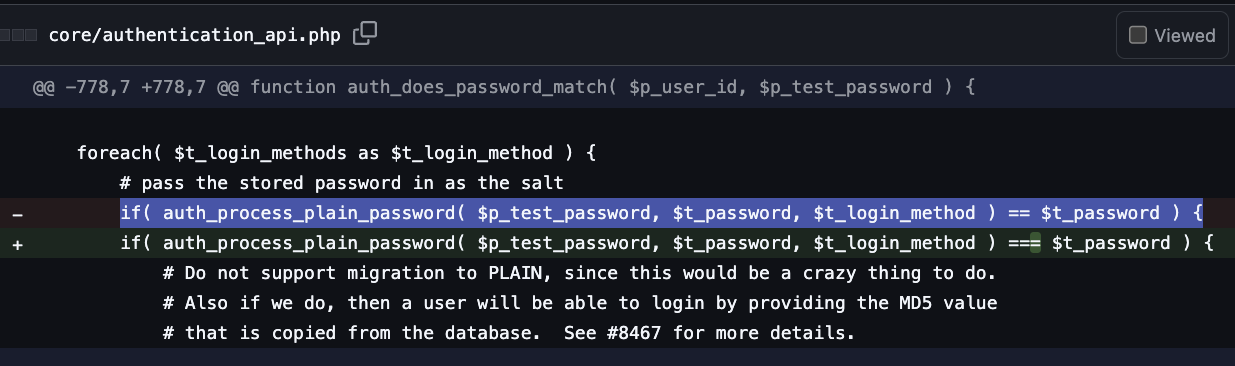
I understand #curl project decision to stop the #bugbounty and leave #hackerone. The torrent of #AIslop has become unbearable.
 I will continue to report vulnerabilities to the project whether it has a bug bounty or not.
I will continue to report vulnerabilities to the project whether it has a bug bounty or not.
GitHub
BUG-BOUNTY.md: we stop the bug-bounty end of Jan 2026 by bagder · Pull Request #20312 · curl/curl
Remove mentions of the bounty and hackerone.
There will be more mentions, blog posts, timings etc in the coming weeks.