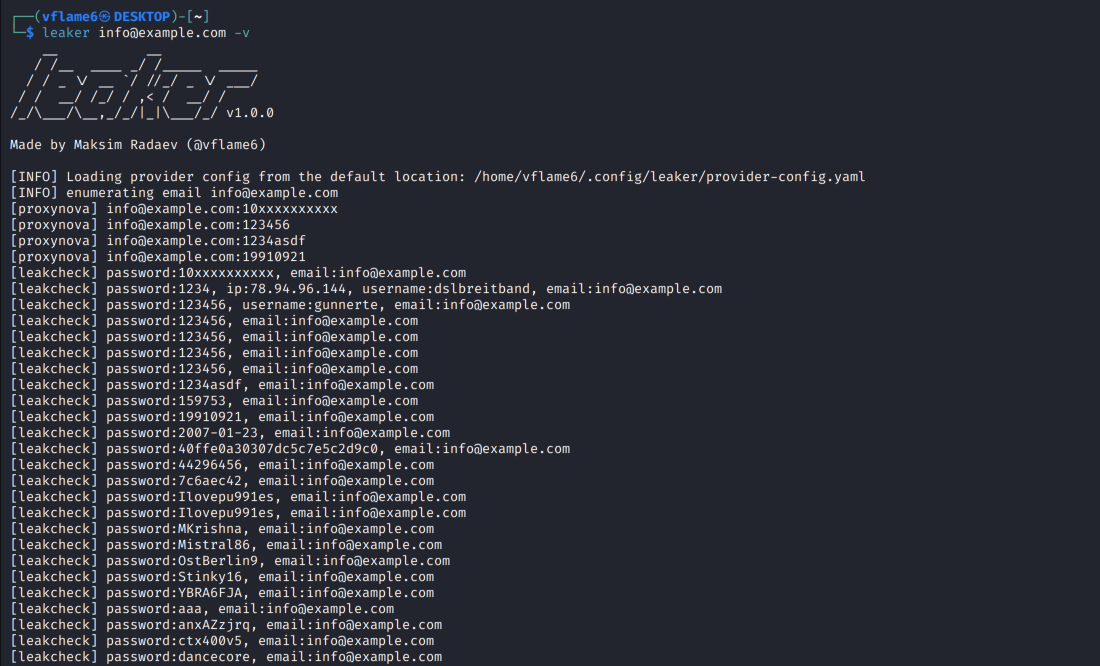
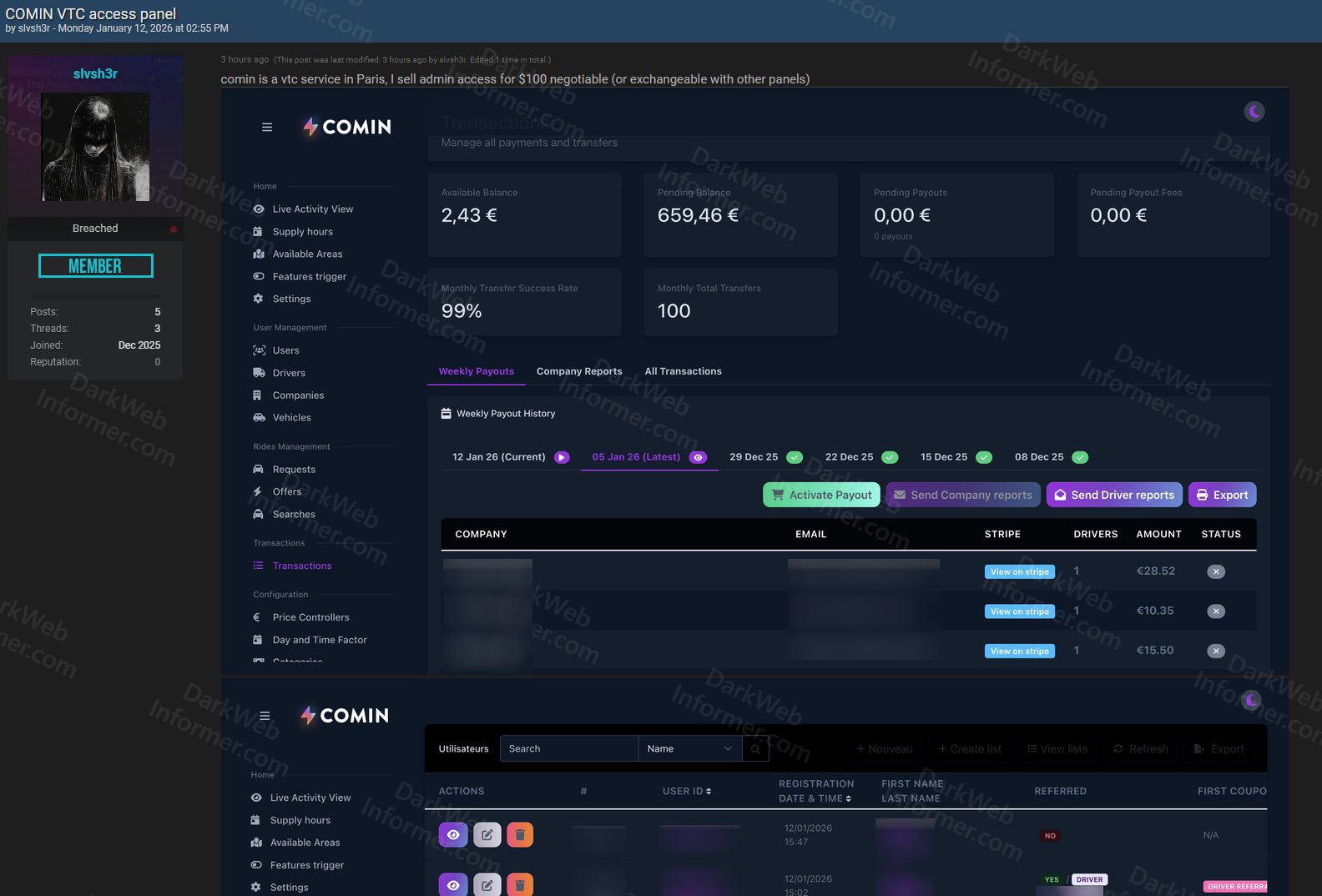
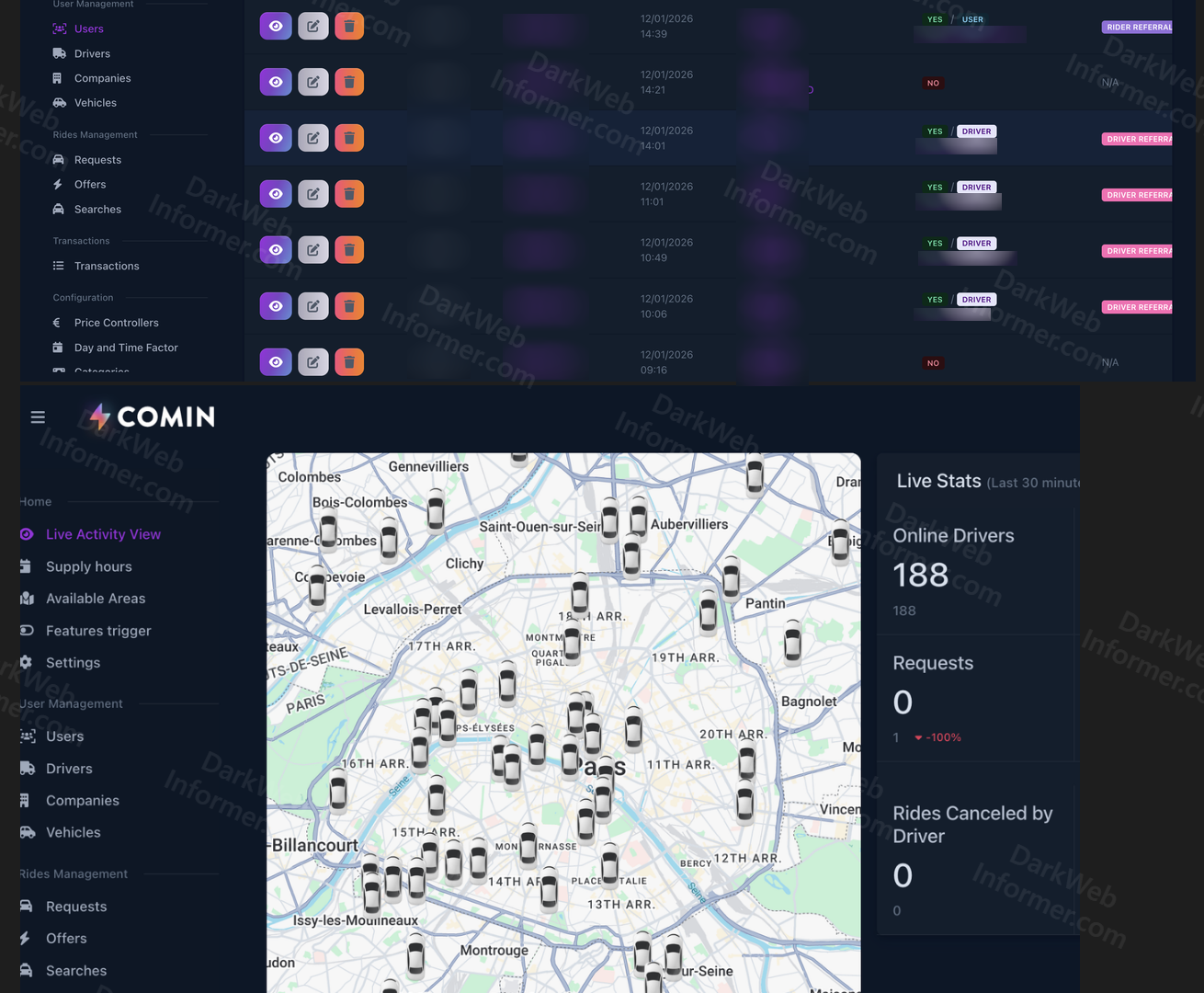
❗️Watched domains for Whiteintel alerts on the website and on the @DarkWebIntelBot have been updated. This list is monitoring United States Government domains. The list below was taken from:
https://flatgithub.com/cisagov/dotgov-data/blob/main/?filename=current-full.csv&sha=08fdf001ad5460bad669b62e254e3b98918fd07b
Watched:
whitehouse.gov, visitthecapitol.gov, visitthecapital.gov, ushouse.gov, uscapitol.gov, uscapital.gov, speaker.gov, senate.gov, sen.gov, republicans.gov, house.gov, gop.gov, dems.gov, democrats.gov, copyright.gov, congress.gov, capital.gov, aoc.gov, ustaxcourt.gov, ussc.gov, usprobation.gov, uscourts.gov, uscavc.gov, usc.gov, usbankruptcy.gov, supremecourtus.gov, supremecourt.gov, supreme-court.gov, scuspd.gov, scus.gov, scinet.gov, scinet-test.gov, sc-us.gov, pacer.gov, judicialconference.gov, fjc.gov, federalrules.gov, federalprobation.gov, federalcourts.gov, fd.gov, cavc.gov, bankruptcy.gov, smithsonian.gov, ns.gov, nic.gov, itis.gov, igorville.gov, dotgov.gov, domainops.gov, dns.gov