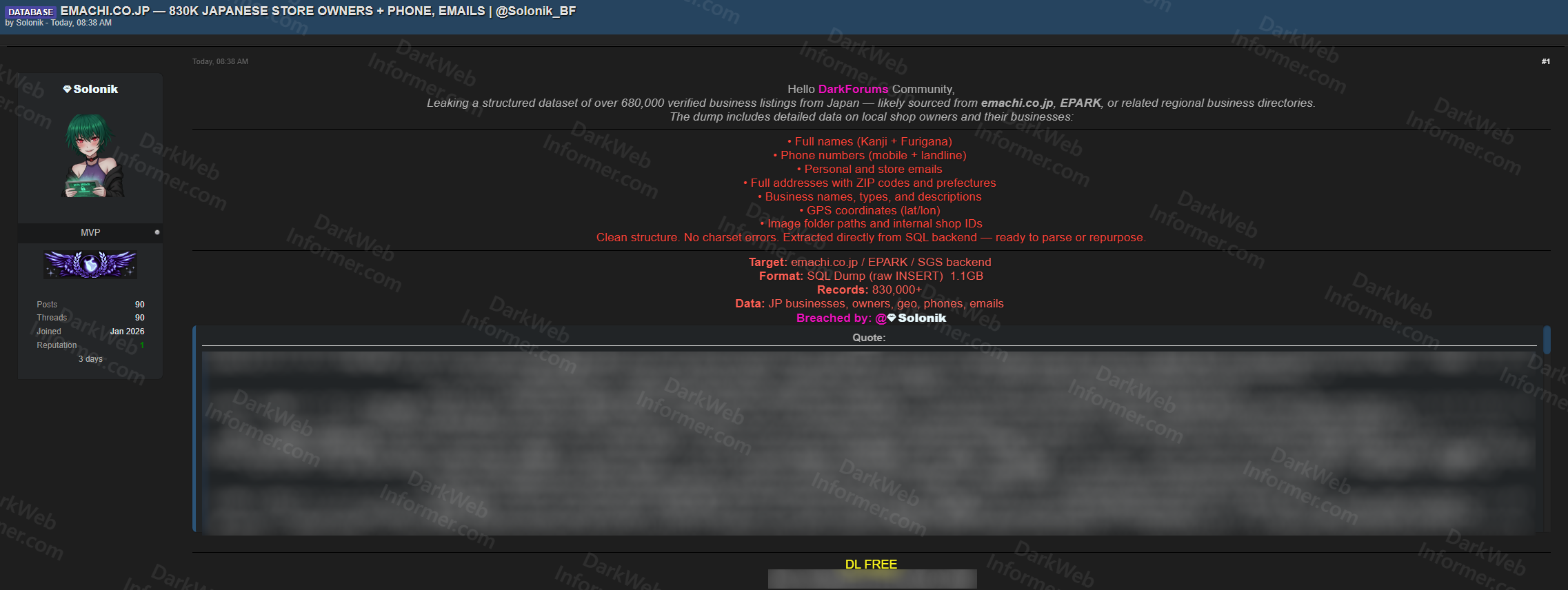
❗️Threat actor allegedly leaking 830K-record dataset tied to Japanese business directories
📌 Japan 🇯🇵
▪️Target: emachi.co.jp
▪️Type: Data Leak
▪️Threat Actor: Solonik
▪️Records: 830,000+
▪️Format: SQL dump (~1.1GB)
▪️Samples: Yes
Data reportedly includes:
▪️Full names (Kanji + Furigana)
▪️Mobile + landline phone numbers
▪️Personal & business emails
▪️Addresses with ZIP codes & prefectures
▪️Business names, types, descriptions
▪️GPS coordinates (lat/lon)
▪️Image folder paths & internal shop IDs