Addy.io: Anonymous Email Forwarding. Protect your real email address using email aliases.
 GitHub:
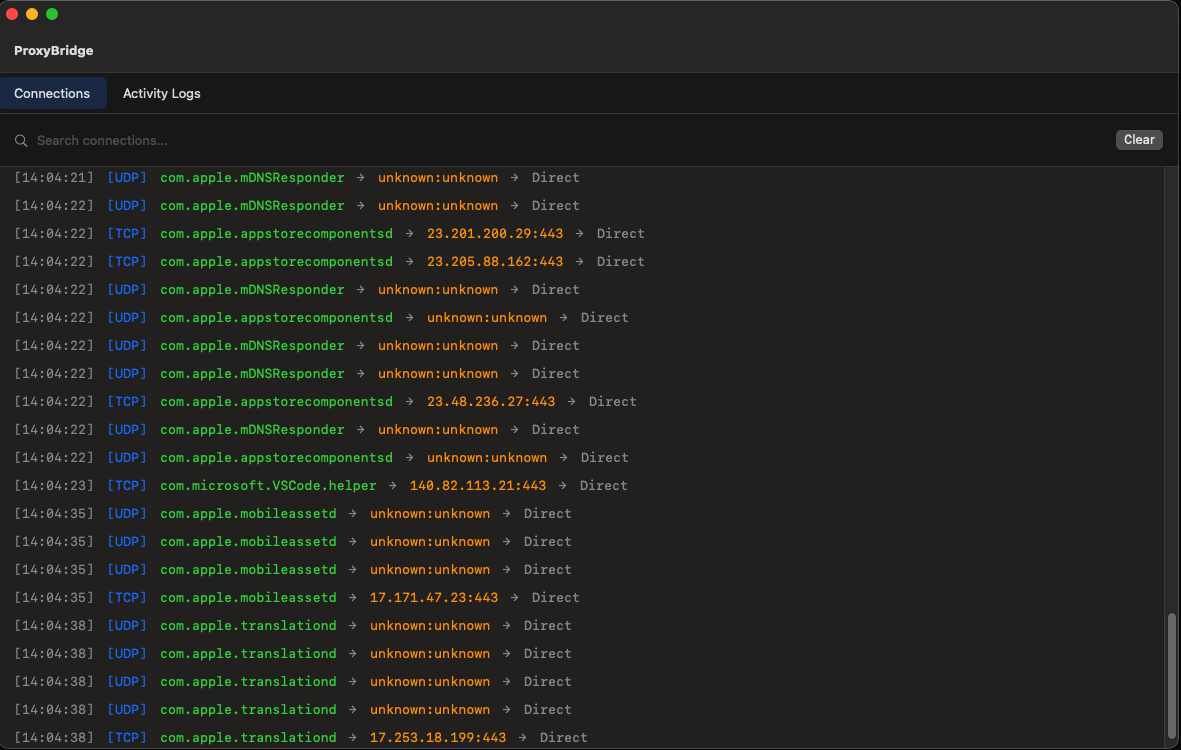
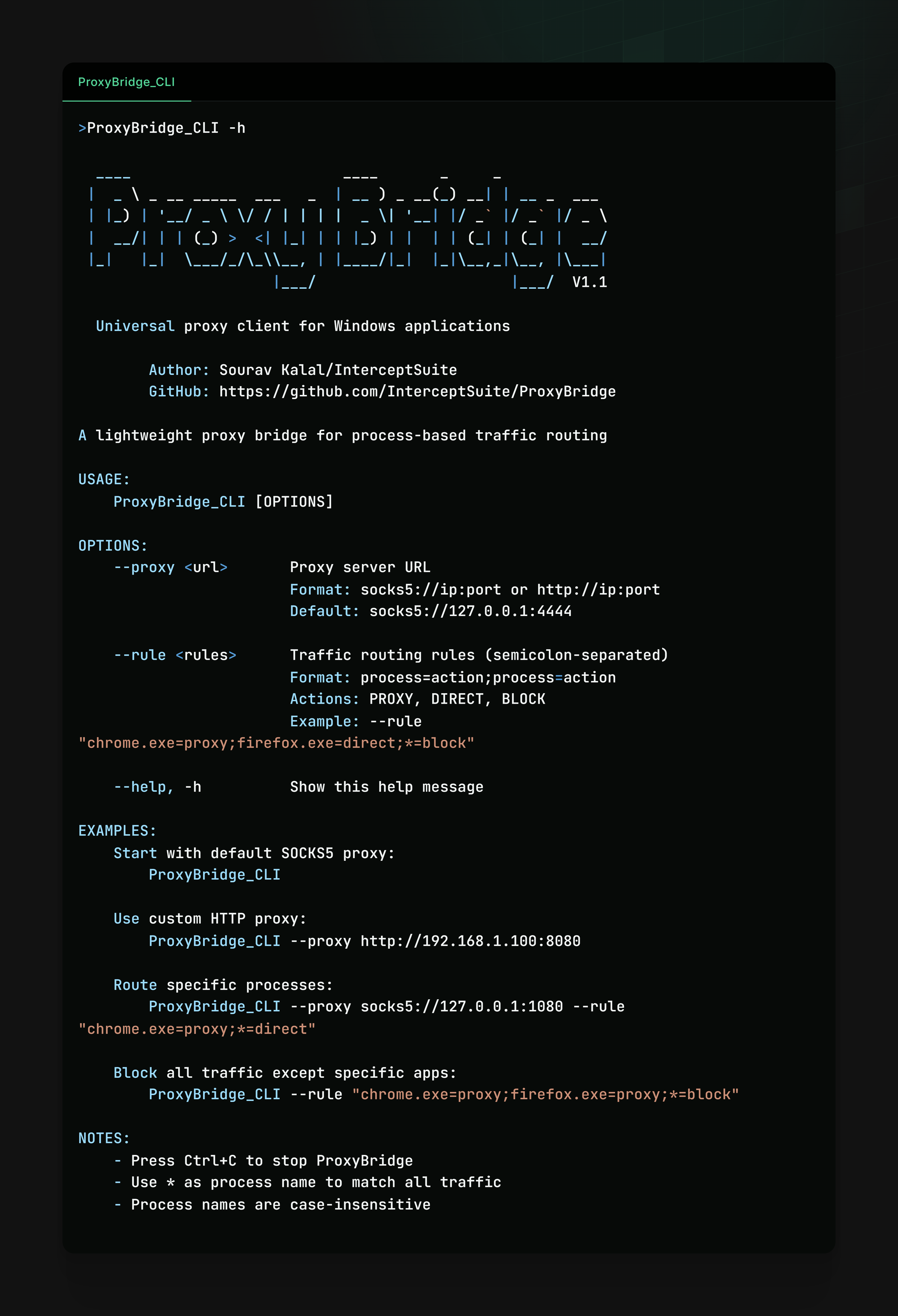
GitHub:  Everyone should be using some sort of burner email address when using different services. It's also very cheap!
There is other choices out there such as SimpleLogin / Proton. Do your own due diligence.
Everyone should be using some sort of burner email address when using different services. It's also very cheap!
There is other choices out there such as SimpleLogin / Proton. Do your own due diligence.
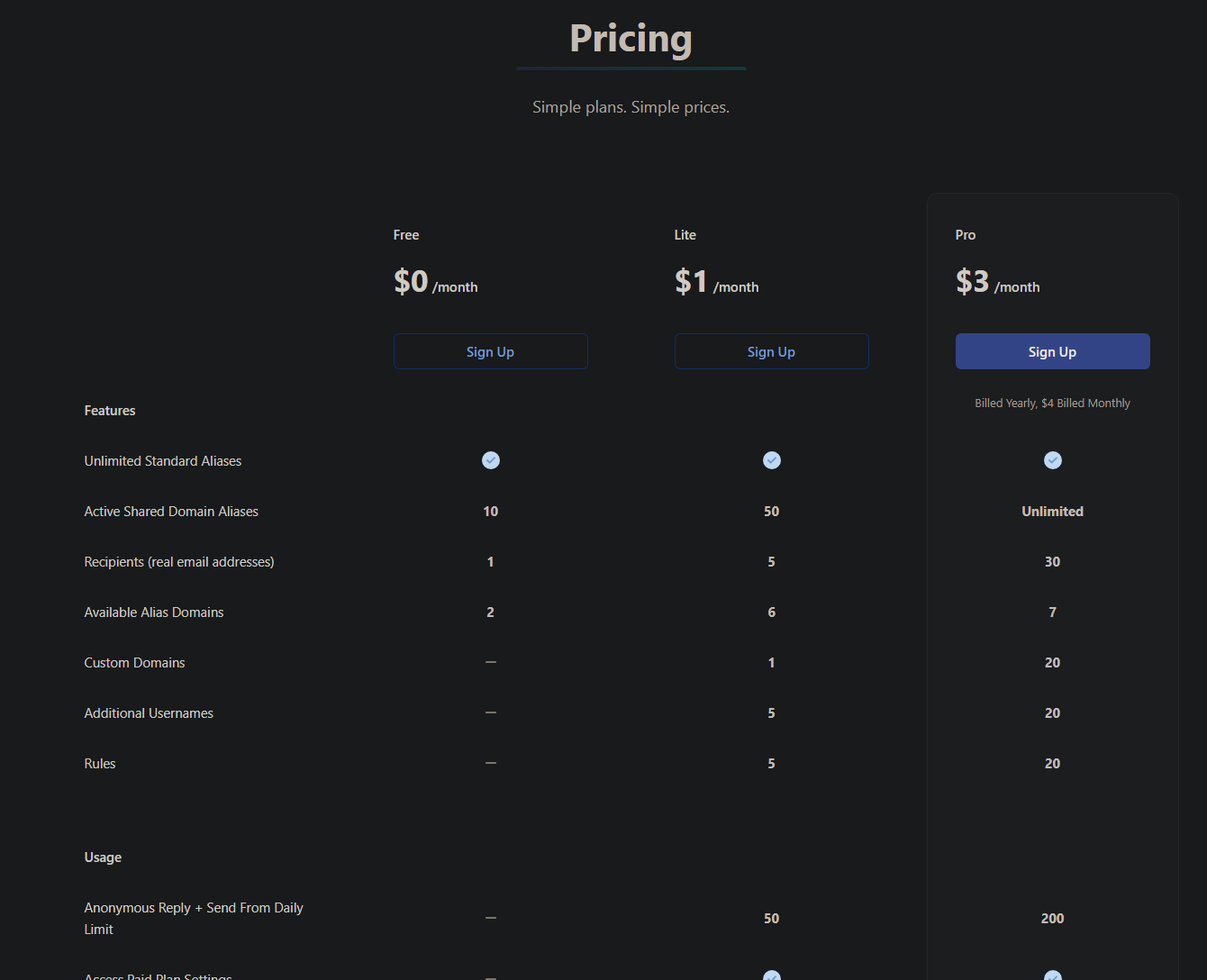

Free, Open-source Anonymous Email Forwarding | addy.io
Create unlimited email aliases for free. Protect your real email from spam by using a different address for each service. Privacy friendly, anonymo...
GitHub
GitHub - anonaddy/anonaddy: Anonymous email forwarding
Anonymous email forwarding. Contribute to anonaddy/anonaddy development by creating an account on GitHub.