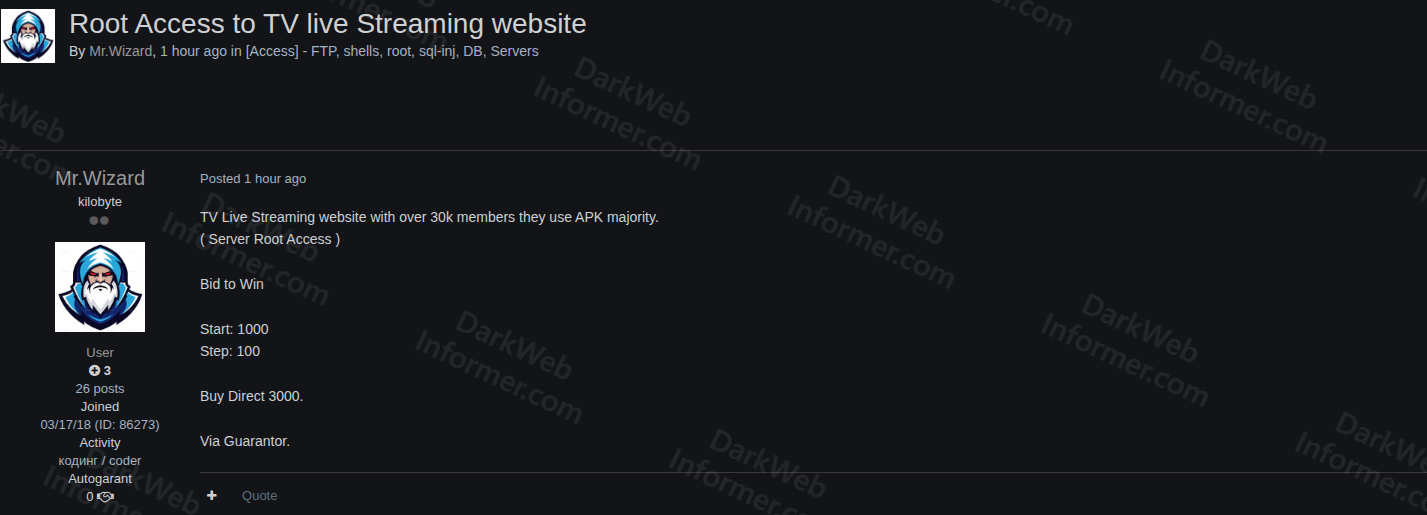
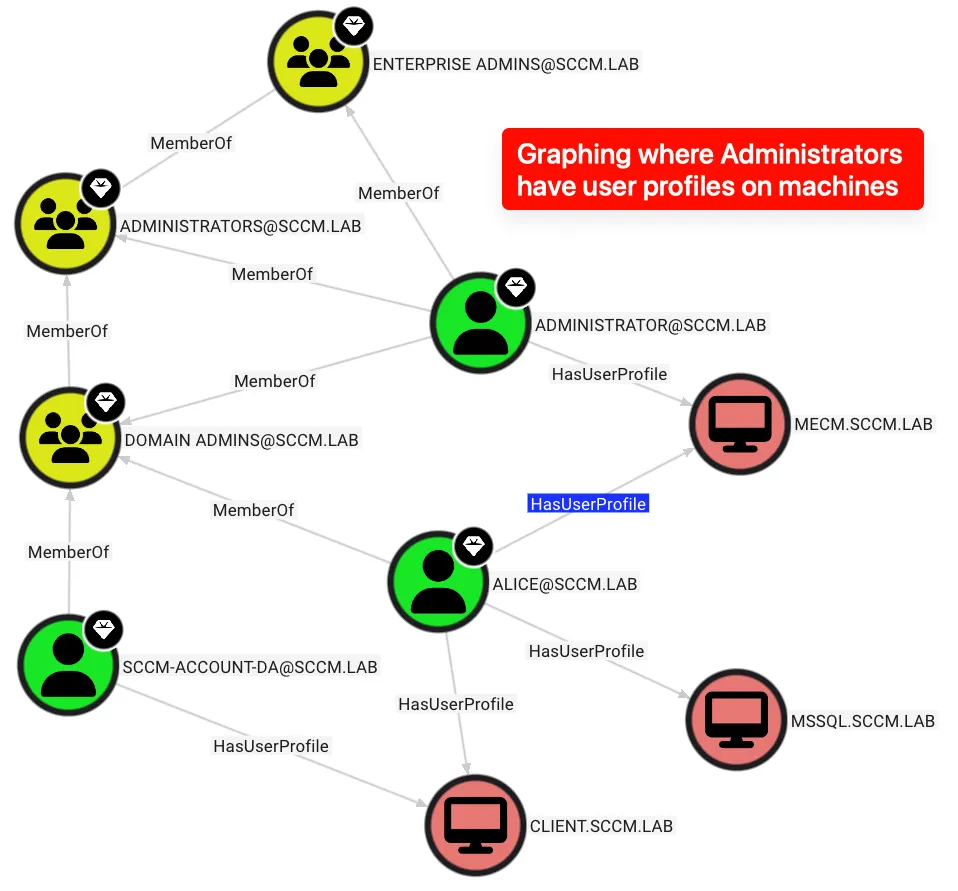
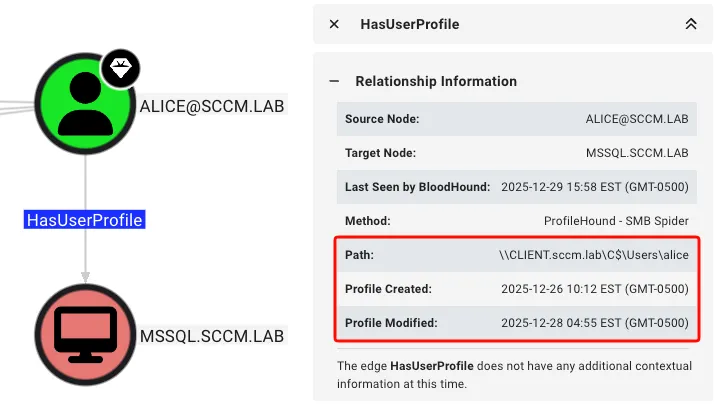
🚨 Threat actor auctions full root access to a TV live-streaming platform with over 30,000 users.
📌 Unknown
▪️Industry: Streaming / IPTV
▪️Type: Server Compromise – Root Access for Sale
▪️Threat Actor: Mr.Wizard
A dark-web actor is offering server-level root access to a TV live-streaming website reportedly serving 30,000+ active users, primarily through an APK-based mobile application.
Offer Details:
▪️Access Level: Full Server Root Access
▪️User Base: 30k+ streaming users
▪️Start: $1,000
▪️Bid Increment: $100
▪️Buy: $3,000