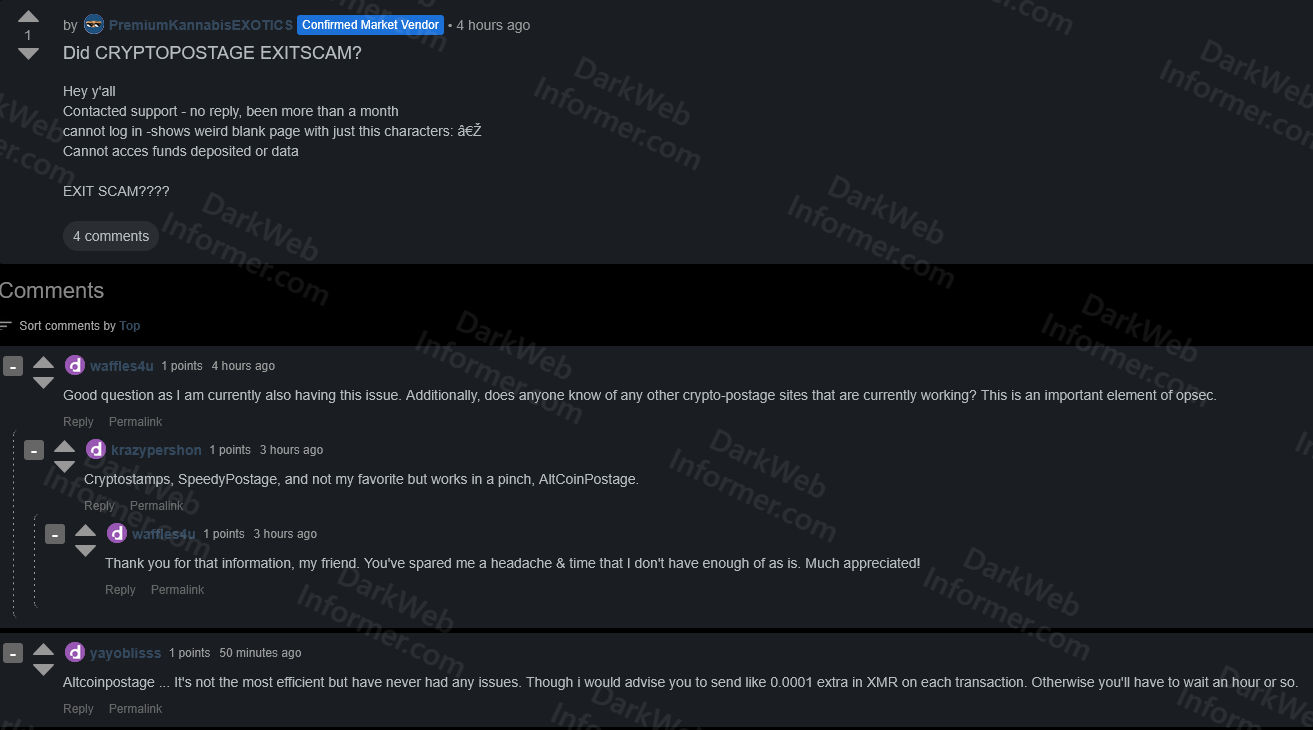
🚨 Threat actor dumps stolen source code allegedly belonging to Rucha Engineers Pvt. Ltd., an Indian automotive engineering and manufacturing partner.
📌 India 🇮🇳
▪️ Company: Rucha Engineers Pvt. Ltd.
▪️ Industry: Automotive Manufacturing / Industrial Engineering
▪️ Type: Source Code Leak
▪️ Threat Actor: 888
▪️ Samples: Yes
Company Overview:
Rucha Engineers specializes in mass-production engineering, automation systems, and industrial solutions. The company supplies or partners with major automotive brands including Audi, Fiat, Nissan, Skoda, and Volkswagen India.