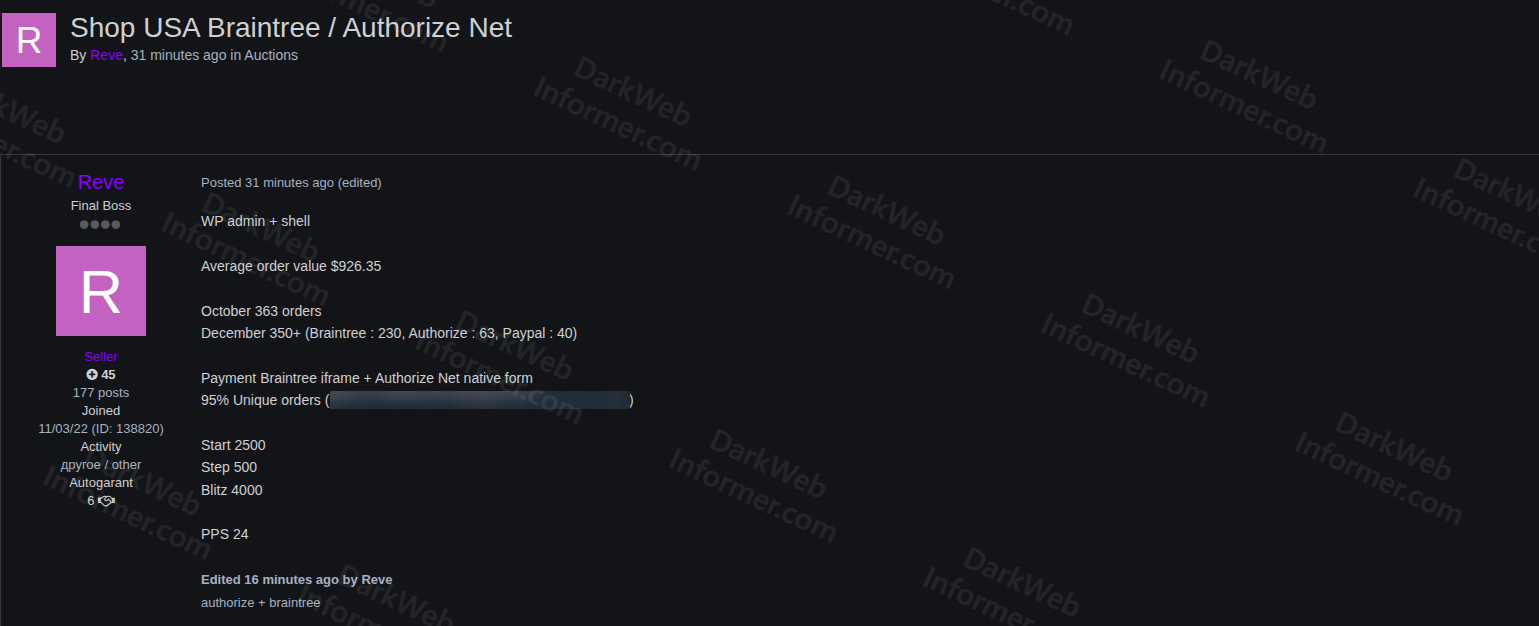
🚨 Threat actor is auctioning WordPress admin + shell access to a US-based online shop, allegedly processing payments via Braintree and Authorize.Net.
📌 United States 🇺🇸
▪️ Platform: WordPress
▪️ Type: Initial Access
▪️ Threat Actor: Reve
▪️ Samples: Yes
Claims include:
▪️ WP admin + shell access
▪️ Braintree iframe + Authorize.Net native form
▪️ Claimed average order value: ~$926
Claimed order volume:
▪️October: 363 orders
▪️December: 350+ orders (Braintree: 230 • Authorize.Net: 63 • PayPal: 40)
▪️ Seller claims ~95% unique orders
Auction details:
▪️ Start: $2,500 • Step: $500 • Blitz: $4,000